OpenID Connect
Auth0 Integration
Auth0 provides single sign-on across applications with two-factor authentication and federation to enterprise identity providers such as Microsoft Active Directory.
Integration with Auth0 is implemented through the auth-openid extension. This integration works also with other OpenID Connect compatible identity providers.
- Before you start with the integration, make sure that users in Auth0 and Guacamole share the same username. Auth0 uses the email address as username by default. The users in Guacamole have be be named accordingly.
- Create a new client (https://manage.auth0.com/#/clients/create) and choose Regular Web Application
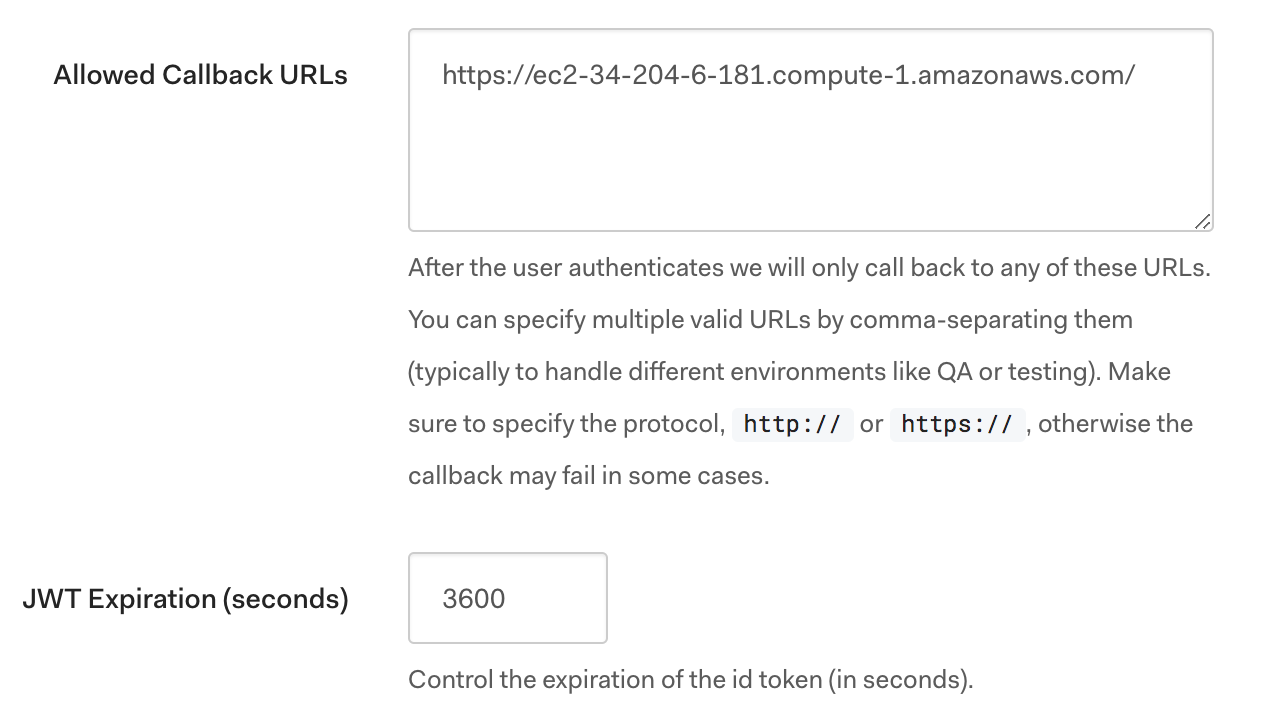
- In the Settings tab, add the Public Hostname of the EC2 instance to the Allowed Callback URLs (e.g. https://ec2-00-00-00-00.compute-1.amazonaws.com/).
- Set the JWT Expiration (seconds) to 3600.
- Enable the OpenID Connect extension by linking the extension into the
extensionsfolder. Execute the following command from/home/ec2-user/guaws. The destination file name (guacamole-auth-0-openid-1.6.0.jar) is important because Guacamole processes the authentication extensions in alphabetical order.
sudo ln -s ../available-extensions/guacamole-auth-sso-1.6.0/openid/guacamole-auth-sso-openid-1.6.0.jar \
/home/ec2-user/guaws/guacamole/etc/extensions/guacamole-auth-0-openid-1.6.0.jar
- Open
/home/ec2-user/guaws/guacamole/etc/guacamole.propertiesand add these properties
# Replace mytenant.auth0.com with your tenant domain
openid-authorization-endpoint=https://mytenant.auth0.com/authorize
openid-jwks-endpoint=https://mytenant.auth0.com/.well-known/jwks.json
# The issuer to expect for all received ID tokens.
openid-issuer=https://mytenant.auth0.com/
# Include your client ID which can be found in the Settings tab
openid-client-id=
# Replace with the Public Hostname of the EC2 instance
openid-redirect-uri=https://ec2-00-00-00-00.compute-1.amazonaws.com/
- Restart Guacamole by executing
guawsctl restart guac. If Guacamole does not come back after the restart command or if signing in fails, review the log files by executingguawsctl logs -f guac. - Visit the public hostname of your EC2 instance and you will be redirected to Auth0 for authentication.